Training & Certs
Achievement
Defcon 2020:Recon village CTF (Placed in the top 10)
CSCV (Cyber Specials Cyber Volunteers) CTF: Challenge coin
Lincoln Hack 2017-19 (Consecutive wins from 2017, 2018 and 2019)
Hack the police (London 2019 & Lincoln 2018)
These challenges have always tested my skills in many ways from OSNIT to teamwork and due to my skills, I have excelled in every hackathon I’ve attended.
I have the skills, passion and determination to pull myself up by my bootstraps. I really get stuck into any problem or project I’m presented with.
Training Taken
Arc-sight Console intensive training
learn about ArcSight and how to use it, including filters, basic principles, management and how to build dashboards.
Ethical Hacking and Penetration Testing with Kali Linux Training Course
Kali Linux, but also covers basic programming, basics of Linux and Linux terminal commands. Viewers will start by installing Kali Linux on a virtual box, and then begin exploring the various tools.
Linux – Learn Linux
Using 8 different projects and a series of examples at every step, you’ll be guided into installing a Linux distro, building your own server and even performing a series of different tasks. That’s not all the course also comes equipped with a series of quizzes that can help you enhance your learning experience and your knowledge at the end of each section.
Art of the Jedi Mind Trick Training Course
In the context of this course, the Jedi Mind Trick is effective communication, or a two-way information sharing process, which involves one party sending a message that is easily understood by the receiving party. Effective communication is a skill needed by everyone, especially when you are trying to convey an important point, namely, security.
Taught by InfoSec Curmudgeon and former DoD Analyst Jeffrey Man, The Art of the Jedi Mind Trick course takes a unique approach to conveying the strategies of effective communication. In an interesting twist, users will be taught fundamental communication skills from the ‘Jedi Master’ who uses many movie references to convey his point.
Exposing Vulnerability Management
Vulnerability Management is the constant practice of identifying, classifying, remediating, and mitigating vulnerabilities. It is an integral part of computer and network security. There are four high level processes that encompass vulnerability management – Discovery, Reporting, Prioritization and Response. Each process and sub processes within it need to be part of a continuous cycle focused on improving security and reducing the risk profile of network assets.
The Complete Cyber Security Course: Hackers
We explore the Dark-net and mindset of the cyber criminal. Covering malware, exploit kits, phishing, zero-day vulnerabilities and much more.
The Complete Cyber Security Course: End Point Protection
Covering all the major platforms Windows, MacOS, Linux, iOS and Android. Master the selection and implementation of solid disk encryption technology to protect devices from disk decryption attacks.
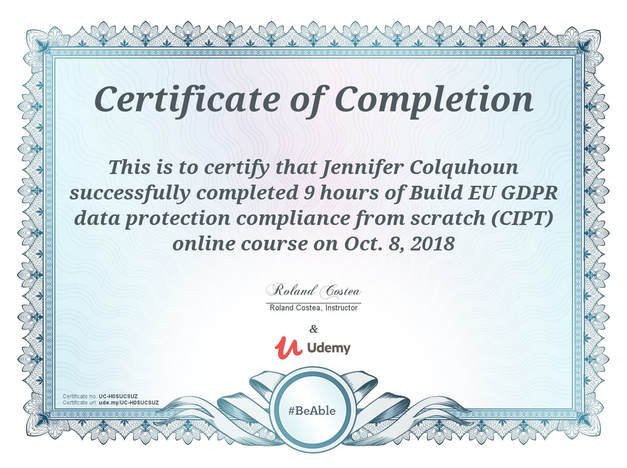
Build EU GDPR Data Protection Compliance From Scratch
The course is a complete A to Z GDPR training, so we will cover everything that you need to know.In this way, we will first create the GDPR implementation plan as a first outcome, then I will teach you the basic theory you need to know for being successful in front of clients or management and also that will help you in achieving your CIPT certification.
Malware Fundamentals Certification Course
- How to recognize common malware
- How to perform dynamic/ static analysis on all major file types
- How to carve malicious executable